Safeguard Your Web Applications with these 31 High-Quality Vulnerability Scanners
Table of Content
A web application vulnerability scanner is an expertly crafted software program, engineered to methodically scan web applications for security vulnerabilities.
It operates with precision, simulating attacks and meticulously observing the application's response to pinpoint potential weak points with absolute certainty.
The scanner isn't just helpful, it's essential for penetration testers ("pentesters"). It's a vital tool that uncovers vulnerabilities, like SQL injection, cross-site scripting (XSS), and cross-site request forgery (CSRF) to name a few.
These vulnerabilities aren't just hypotheticals, they're actual weak spots that could be exploited by attackers. By identifying these vulnerabilities early, pentesters aren't just fixing issues, they're proactively fortifying the web application's defenses, thereby elevating its security.
Similarly, for web application developers, a vulnerability scanner is an essential tool for maintaining the security of their applications. Developers are not usually security experts, and it is easy for them to overlook potential security threats. By using a scanner, they can ensure that their applications are as secure as possible, even if they are not experts in every potential attack vector.
In this post, we will explore the best 30+ open-source free web scanner app that enables pentesters, and web app developers to scan their web apps for security vulnerabilities.
1. RapidScan
RapidScan is a free and open-source command-line toolset that allows pentesters and web developers to check for security issues in web apps easily.
It is easy to install, configure and use, and comes with dozens of useful tools that include nmap, dnsrecon, wafw00f, uniscan, sslyze, fierce, lbd, theharvester, amass, nikto etc executes under one entity.
It requires Python3 and Kali Linux, but you can also install it on any Debian, Ubuntu, Fedora or Arch -based distros. Personally, I tested it with macOS, and it works flawlessly.
Vulnerability Checks
- DNS/HTTP Load Balancers & Web Application Firewalls.
- Checks for Joomla, WordPress and Drupal
- SSL related Vulnerabilities (HEARTBLEED, FREAK, POODLE, CCS Injection, LOGJAM, OCSP Stapling).
- Commonly Opened Ports.
- DNS Zone Transfers using multiple tools (Fierce, DNSWalk, DNSRecon, DNSEnum).
- Sub-Domains Brute Forcing (DNSMap, amass, nikto)
- Open Directory/File Brute Forcing.
- Shallow XSS, SQLi and BSQLi Banners.
- Slow-Loris DoS Attack, LFI (Local File Inclusion), RFI (Remote File Inclusion) & RCE (Remote Code Execution).

2. Vuls (Software Update Vulnerabilities)
Vuls is a free tool designed to assist system administrators in managing security vulnerabilities and software updates.
It automatically detects vulnerabilities, identifies affected servers, and generates regular reports, thereby reducing the risk of oversight and the burden of manual monitoring and analysis.
It comes with a rich notification module that inform the user automatically through Slack bot or emails.
The project is originally generated in a Google Summer of Code event.
Supported systems
- Alpine, Amazon Linux, CentOS, AlmaLinux, Rocky Linux, Debian, Oracle Linux, Raspbian, RHEL, openSUSE, openSUSE Leap, SUSE Enterprise Linux, Fedora, and Ubuntu
- FreeBSD
- Windows
- macOS
- Cloud, on-premise, Running Docker Container
3. Nettacker wit IoT Scanner
The OWASP Nettacker project automates information gathering, vulnerability scanning, and report generation for networks.
It uses TCP SYN, ACK, ICMP, and other protocols to detect and bypass Firewall/IDS/IPS devices. Its unique method for discovering protected services and devices, such as SCADA, gives it a competitive edge over other scanners.
It features a command-line interface (CLI), web interface, and a RESTful API, and it supports HTML, JSON, CSV and TEXT outputs out-of-box.
IoT Scanner Features
- Python Multi Thread & Multi Process Network Information Gathering Vulnerability Scanner
- Service and Device Detection ( SCADA, Restricted Areas, Routers, HTTP Servers, Logins and Authentications, None-Indexed HTTP, Paradox System, Cameras, Firewalls, UTM, WebMails, VPN, RDP, SSH, FTP, TELNET Services, Proxy Servers and Many Devices like Juniper, Cisco, Switches and many more… )
- Asset Discovery & Network Service Analysis
- Services Brute Force Testing
- Services Vulnerability Testing
- HTTP/HTTPS Crawling, Fuzzing, Information Gathering and …
- HTML, JSON, CSV and Text Outputs
- API & WebUI
4. Scanners Box
Scanners Box, also known as scanbox, stands as a formidable hacker toolkit. It has amassed an impressive collection of open-source scanners from Github, encapsulating more than 10 categories, including subdomain, database, middleware, and others, all in a modular design.
However, it's important to note that other well-known scanning tools, such as nmap, w3af, brakeman, arachni, nikto, metasploit, aircrack-ng, are not included in our collection scope.
5. VulnAPI (API Vulnerability Scanner)
VulnAPI is a free open-source Dynamic Application Security Testing (DAST) tool designed to scan APIs for common security vulnerabilities. It offers two methods for scanning APIs: using Curl-like CLI and OpenAPI contracts.
6. VulnScan (Scan with ChatGPT)
VulnScan, a powerful vulnerability scanning tool, aids website owners in protecting their sites from cyber threats.
It uses advanced technology, including OpenAI's AI language model, ChatGPT, to check JavaScript for vulnerabilities, allowing for early detection and correction before exploitation by cybercriminals.
7. Raccoon

Raccoon is an offensive security tool for reconnaissance and information gathering. It provides DNS details, WHOIS information, TLS data, port scanning, services and scripts scanning, URL fuzzing, subdomain enumeration, and web application data retrieval including CMS detection.
8. Trivy
Trivy is a free and open-source comprehensive and versatile security scanner. Trivy has scanners that look for security issues, and targets where it can find those issues.
Targets (what Trivy can scan):
- Container Image
- Filesystem
- Git Repository (remote)
- Virtual Machine Image
- Kubernetes
- AWS
Scanners (what Trivy can find there):
- OS packages and software dependencies in use (SBOM)
- Known vulnerabilities (CVEs)
- IaC issues and misconfigurations
- Sensitive information and secrets
- Software licenses
9- Kics
KICS (Keeping Infrastructure as Code Secure) by Checkmarx isn't just another open-source tool.
It's a formidable weapon that identifies security vulnerabilities, compliance issues, and infrastructure misconfigurations in the early development cycle of infrastructure-as-code. This makes it an indispensable asset for any cloud native project.
Supported Systems
- Docker
- Kubernetes
- Terraform
- AWS CloudFormation
- OpenAPI
- Ansible
- AWS Cloud Development Kit
- Crossplane
- Pulumi
- Serverless
- OpenTofu
- gRPC
- GitHub
10. VulnX
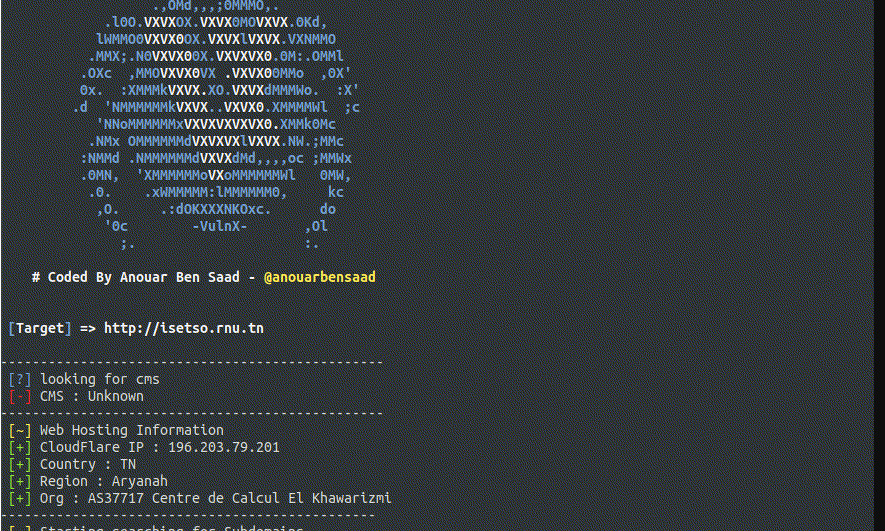
VulnX stands as a superior Intelligent Bot Auto Shell Injector, masterfully detecting vulnerabilities in a multitude of CMS types. Boasting rapid CMS detection, extensive information gathering, and incisive vulnerability scanning, it targets and identifies subdomains, IP addresses, country, organization, timezone, region, and much more...
Contrary to other tools that rely on manual shell injection, VulnX revolutionizes the process by carefully analyzing the target website.
Upon identifying a vulnerability, the shell is promptly injected. Additionally, it excels in URL searching with its sophisticated dorks tool.
It is an ideal solution to scan for many popular CMS such as WordPress, Joomla, Magento, OpenCart, Prestashop, Drupal, and more.
VulnX comes in two modes, the URLSET mode and the DORKSet mode.
It is easy to install from source or using Docker, and comes with a memory-friendly command line options.
Features
- Detects CMS engine
- Target informations gatherings
- Target Subdomains gathering
- Multi-threading on demand
- Checks for vulnerabilities
- Auto shell injector
- Exploit dork searcher
Ports ScanHigh LevelDns-Servers Dump- Input multiple target to scan.
- Dorks Listing by Name& by ExploitName.
- Export multiple target from Dorks into a logfile.
11. Secator
Secator isn't just a task and workflow runner, it's your steadfast companion for security assessments.
With support for a multitude of acclaimed security tools, Secator is engineered to not just enhance productivity, but to revolutionize the work of pentesters and security researchers.
It comes with dozens of useful tools that enables pentesters to scan web apps, API endpoints, DNS, subdomain finder, and several OSINT tools.
Features
- Curated list of commands
- Unified input options
- Unified output schema
- CLI and library usage
- Distributed options with Celery
- Complexity from simple tasks to complex workflows
- Customizable
12. Apache Block Bad Bots
The Ultimate Apache Block Bad Bots is more than a scanner tool, it stands out as an all-encompassing blocker tool, unequivocally barring bad bots, user-agents, spam referrers, adware, malware, ransomware, clickjacking, click redirecting, SEO companies, and bad IPs from infiltrating your websites.
A robust Anti-DDoS system, Nginx rate limiting, and Wordpress theme detector blocking are also incorporated, providing an unassailable fortress for your online presence.
13. Jie
Jie confidently positions itself as an authoritative security assessment and exploitation tool, specifically designed for web applications.
Its powerful array of features, which includes vulnerability scanning, information gathering, and exploitation, unequivocally establishes it as an essential asset for security professionals and penetration testers.
It comes with two modes, passive mode or security copilot, and Vulnerability Exploitation mode.
14. Faraday
Faraday is an open-source (GPL-3.0) self-hosted security tool designed to assist in discovering vulnerabilities and organizing findings. It operates in your terminal, allowing for real-time organization.
Faraday also aggregates and normalizes data for exploration in various visualizations, catering to both managers and analysts. It is an open-source vulnerability management platform.
15. SQLMap
sqlmap is a robust open source penetration testing tool that excels in automating the detection and exploitation of SQL injection flaws and commandeering database servers.
It boasts a potent detection engine and a plethora of unique features designed for the consummate penetration tester.
The tool is equipped with an extensive array of switches, encompassing everything from database fingerprinting and data fetching, to accessing the underlying file system and executing commands on the operating system via out-of-band connections.
Download
16. Nuclei Plan Your Pentests using YAML Templates
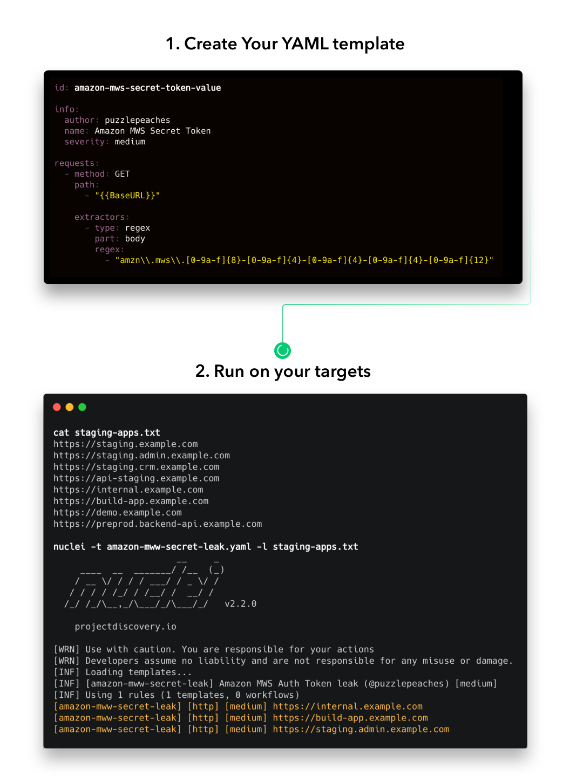
Nuclei (a free and open-source tool) confidently delivers requests across targets based on a template, ensuring zero false positives and lightning-fast scanning across a multitude of hosts.
With its capacity to scan a broad spectrum of protocols including TCP, DNS, HTTP, SSL, File, Whois, Websocket, Headless, and Code, Nuclei stands out in its field. Its powerful and adaptable templating can model any security check, proving its robust and versatile nature.
17. Commix
Commix, an abbreviation of [comm]and [i]njection e[x]ploiter, is a robust open-source penetration testing tool. Authored by the esteemed Anastasios Stasinopoulos (@ancst), it confidently automates the detection and exploitation of command injection vulnerabilities.
18. KillShot

KillShot is more than just a penetration testing framework - it's a potent instrument for data collection and detecting website vulnerabilities. With its capacity to spider websites for automated data collection, identify the CMS, and discover vulnerabilities, it revolutionizes the field.
It conducts a variety of scans using nmap and unicorn, ensuring extensive coverage. Additionally, it can create basic PHP backdoors, enhancing its practicality.
This tool also houses a basic Ruby Fuzzer, tested on VULSERV.exe, and a Linux log clear script that can alter login paths. KillShot is the ultimate tool in your cybersecurity toolkit.
19. XAttacker
XAttacker V2.5 serves as an undisputed tool for scanning and systematically exploiting vulnerabilities in web applications.
It capably discerns the architecture of a target website, identifies potential vulnerabilities rooted in the detected Content Management System (CMS), and confidently generates an exploit.
It boasts sought-after features such as vulnerability scanning, auto-exploiting, CMS attacking, dork searching with multiple search engines, and succinct plain text reporting.

20. Safety CLI (Secure Python Apps)
Safety CLI is an unrivaled Python dependency vulnerability scanner. It excels at detecting packages with known vulnerabilities and malicious packages, and it offers robust remediation recommendations.
Harnessing a comprehensive database of vulnerabilities, it's the go-to tool for pentesters and devOps. For scanning Python packages, there's simply no comparison.

21. DDos Ripper
A Distributable Denied-of-Service (DDoS) attack is a server that inundates targets with a flood of internet traffic, effectively cutting them off.
This is achieved using multiple compromised computer systems, including computers and IoT devices, as a source of attack traffic. It can be likened to an unexpected traffic jam that prevents regular traffic from reaching its destination.

22. DVWA
Damn Vulnerable Web Application (DVWA) is a savvy PHP/MySQL application deliberately designed with vulnerabilities. It's a powerful tool for security professionals, web developers, students, and teachers to gain a deep, hands-on understanding of web application security.
It showcases a wide range of common web vulnerabilities, presenting varying difficulty levels. Both documented and undocumented issues are included, providing an unmatched opportunity for users to delve into the complexities of web security.
23. JSQL Injection
jSQL Injection is a robust, lightweight application expertly designed to extract database information from a server.
This powerful tool is not only free and open source, but also cross-platform compatible with Windows, Linux and Mac, seamlessly functioning with Java versions 11 to 20.
Proudly, jSQL Injection is an integral part of the official penetration testing distribution Kali Linux, and is included in a number of other esteemed distributions such as Blackbuntu, Pentest Box, Parrot Security OS, ArchStrike and BlackArch Linux.
24. Wscan
Wscan, the revolutionary web security scanner, is leading the charge in democratizing web security. Harnessing the power of machine learning for penetration testing, it masterfully learns attack and defense patterns to launch highly targeted attacks.
This innovative strategy dramatically elevates efficiency, sharpens accuracy, and minimizes bothersome false positives. Capable of handling vast amounts of data, Wscan expertly identifies vulnerabilities and swiftly adapts to emerging attack patterns. We are firm in our belief that machine learning in penetration testing is the undisputed future of network security.
It supports passive and active scan modes, and comes with feature-rich reporting model.
25. DamnWebScanner
The Damn Web Scanner is a robust Chrome and Opera extension, expertly engineered to scan for web vulnerabilities. It efficiently uncovers threats such as SQL Injection, Cross Site Scripting, Local File Inclusion, and Remote Commands Execution.
Operating diligently in the background, it promptly notifies users of any detected vulnerabilities, ensuring your web security is never compromised.
Key Features
- Detect if the server is up with a "/ping" request
- New XSS vectors, work in different contexts (JS var, JS function, inside HTML tag, outside HTML tag)
- Basic page to list the vulnerabilities URL and TYPE
- Re-use your cookies and user-agent to get access to page with cookie-authentication
- Export vulnerabilities into a CSV file
- Launch scan when a form is submitted or a page is opened via the URL bar
26. SQLi-Hunter
SQLi-Hunter is the definitive HTTP/HTTPS proxy server and SQLMAP API wrapper, designed to streamline and simplify the process of identifying SQLi.
SQLi-Hunter can be easily installed using Docker or from source.
27. Vulnerable Client-Server Application (VuCSA)
The Vulnerable Client-Server Application (VuCSA) is a robust Java-based platform built specifically for the purpose of mastering and showcasing penetration testing techniques on non-http client-server applications.
It confidently presents a range of challenges including SQL injection, command execution, buffer over-read, enumeration, XML vulnerabilities, horizontal and vertical access control, and RCE deserialization.
28. Zeus (Recommended)
Zeus is a formidable reconnaissance tool crafted to streamline web application reconnaissance.
Zeus boasts an impressive built-in URL parsing engine, compatibility with numerous search engines, the capability to extract URLs from both ban and webcache URLs, the proficiency to execute multiple vulnerability assessments on the target, and the power to overcome search engine captchas.
Features
- A powerful built in URL parsing engine
- Multiple search engine compatibility (
DuckDuckGo,AOL,Bing, andGoogledefault isGoogle) - Ability to extract the URL from Google's ban URL thus bypassing IP blocks
- Ability to extract from Google's webcache URL
- Proxy compatibility (
http,https,socks4,socks5) - Tor proxy compatibility and Tor browser emulation
- Parse
robots.txt/sitemap.xmland save them to a file - Multiple vulnerability assessments (XSS, SQLi, clickjacking, port scanning, admin panel finding, whois lookups, and more)
- Tamper scripts to obfuscate XSS payloads
- Can run with a custom default user-agent, one of over 4000 random user-agents, or a personal user-agent
- Automatic issue creation when an unexpected error arises
- Ability to crawl a web page and pull all the links
- Can run a singular dork, multiple dorks in a given file, or a random dork from a list of over 5000 carefully researched dorks
- Dork blacklisting when no sites are found with the search query, will save the query to a blacklist file
- Identify WAF/ IPS/ IDS protection of over 20 different firewalls
- Header protection enumeration to check what kind of protection is provided via HTTP headers
- Saving cookies, headers, and other vital information to log files
29. Cracker-Tool (Termux-Tools)
Introducing a Termux-Tool, meticulously crafted in Python & Bash programming by the seasoned developer, CRACKER911181. Designed for hacking and penetration testing, this tool stands as an archetype of its kind.
As the creator, I endorse its utilization for ethical purposes only, absolving myself from any misuse thereof. Exclusively for Termux Users.
Features
- IP Tool
- Subdomain Scanner
- Ddos Attack Tool
- Admin Finder
- Hash Cracker
- Video Downloader
- SQL Injection Tool
- Text To Voice Converter
- Python Obfuscator
- Telegram Kit
- Termux Framework
- Kali Nethunter Installer
- Termux Tool
- URL Changer
- URL Shortener
- WEB Tool
- Temporary Mail
- Gmail Generator
- Identity Generator
- Multi Ddos
- Anonymous Share
- Email Tool
- Credit Card Tool
- ZIP Password Cracker
- Ddos with Cloudflare Bypass
30. Black Widow
Black-widow confidently stands as an open-source, Python-based offensive penetration testing tool. It boasts features such as a localhost Web GUI, sniffing, website crawling, and web page parsing.
With continuous updates and extensions, it embodies adaptability. Installation is a breeze, thanks to Docker and Docker-compose.
31. SQLifinder
sqlifinder is a feature-rich tool, expertly designed to detect GET-based SQL Injection vulnerabilities in web applications. It employs waybackurls, web crawlers, and SQL Injection payloads to ensure thorough and reliable vulnerability detection.
It is written using Python and requires Python3 to install and run.