9 Open-source Projects to Turn Raspberry Pi as a Portable Hacking Device
Table of Content
The Raspberry Pi is a versatile, portable single-board computer (SBC) that can be used for almost anything—from building your own CCTV surveillance system or music streaming server to retro gaming consoles or even a private VPN to maintain your privacy.
Even a Door intercome system, yes you can do that.
But what about using it as a portable hacking device? Many enthusiasts have done just that—not only with the Raspberry Pi 3, 4, and 5 but also with the compact Raspberry Pi Zero.
In this post, we explore the best ways to transform your Raspberry Pi into a portable hacking tool.
This article, along with the tools and projects mentioned, is intended strictly for ethical purposes such as penetration testing, security research, and educational learning.
We do not condone, endorse, or encourage any use of these tools for illegal activities, unauthorized access, or hacking others' systems.
1- Mobile Pen(etration) (Rasp)Berry(Pi)
MobilePenBerry is a lightweight, open-source project designed to transform a Raspberry Pi into a mobile penetration testing device. This tool harnesses the portability of Raspberry Pi models, such as the Raspberry Pi Zero, to deliver ethical hacking capabilities on the go.
MobilePenBerry aims to provide a compact and flexible solution for security researchers and penetration testers. The project includes tools to perform various tasks, including network reconnaissance, wireless testing, and vulnerability scanning.
With support for well-known utilities, MobilePenBerry enables ethical hackers to execute tasks like packet capturing, port scanning, and password auditing directly from their portable device.
One of its key features is its integration with Wi-Fi auditing tools like Aircrack-ng, which allows the device to identify and test wireless networks. In addition, it can support services like SSH and VPNs, ensuring secure remote connections to the Raspberry Pi during testing.
The project's simplicity makes it suitable for developers and cybersecurity enthusiasts interested in mobile pentesting setups. Since it leverages the hardware of Raspberry Pi SBCs, it provides an affordable and accessible entry into portable penetration testing.
2- Pi-Pwner
Pi-Pwner is a bash script that will load a comprehensive suite of pentesting tools and scripts onto a Raspberry Pi running Raspbian Stretch.
At the end of the Deployments you will have a set of tools that will help during a penetration testing engagement to perform information gathering, sniffing, spoofing, wireless attacks, post-exploitation and more.
Pi-Pwner loads tools like:
- Kismet
- aircrack-ng
- nmap
- sqlmap
- macchanger
- Bettercap
- nikto
- Responder
- dmitry
- yersinia
- Metasploit-Framework
- And much more
Other tools and scripts include:
- theHarvester
- Exploit-Database
- Golismero
- RouterSploit
- Relayer (Automated SMB Relay attack Script)
- One-Lin3r
- And more
3- ThePwnPal
ThePwnPal is an open-source project designed to transform a Raspberry Pi into a portable penetration testing device. It combines the lightweight portability of Raspberry Pi with the full power of Kali Linux to allow on-the-go ethical hacking and network assessments.
Inspired by the Pwnagotchi Project, ThePwnPal provides the same tools as a complete Linux desktop in a compact format, with added flexibility for mobile pentesting and remote attacks.
Features
- Raspberry Pi Integration: Utilizes the Raspberry Pi for its compact size and portability.
- Standalone Power: Includes a battery with 5000mAh and output current of 3A, providing 8 - 10 hours of consistant power.
- Integrated Display: Compact touchscreen display for improved user interface.
- Extensive range: Supports both 2.4 Ghz and 5 Ghz bands with packet injection and monitor mode.
- Mobile Accessibility: Conduct security assessments and penetration tests from a stealthy handheld device.
- Kali Linux: Configured with Kali Linux tools for a comprehensive penetration testing environment.
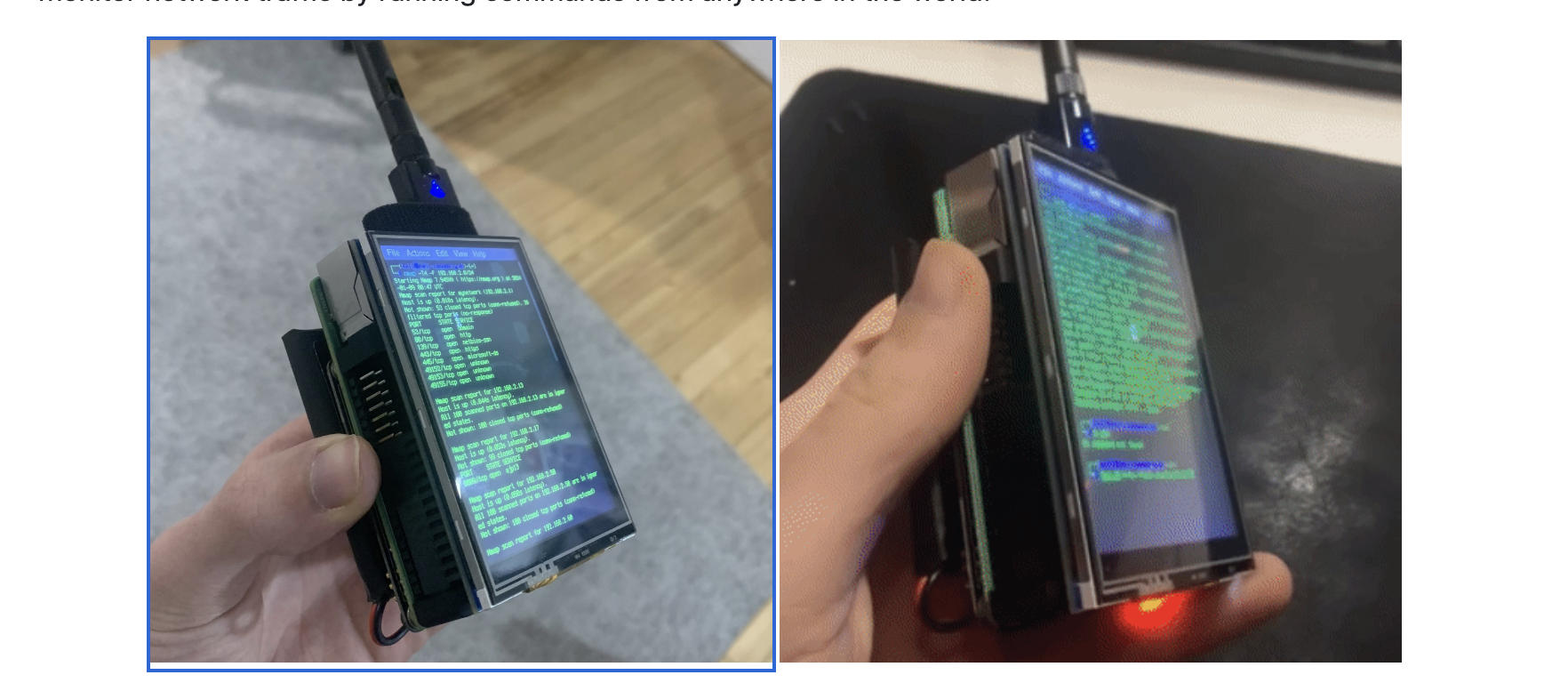
4- Raspwn OS
Raspwn OS is a specialized GNU/Linux distribution designed for training in ethical hacking. It runs on Raspberry Pi 2B or 3, emulating a vulnerable server environment inspired by Damn Vulnerable Linux.
The project is Built on a Debian snapshot from 2015, it includes outdated libraries and services intentionally left vulnerable.
Users can practice both offensive and defensive hacking techniques locally without internet access. The Raspwn Web Playground adds vulnerable web apps on top of the LAMP stack, making it a safe, low-cost environment for penetration testers and learners, all for around $50.
Raspwn emulates a vulnerable Debian Wheezy server. To use it just boot Raspwn then connect to the 'RasPwn OS' WiFi SSID. (Password - 'In53cur3!') from your favorite pen-testing set-up. Once you have connected you can explore the 192.168.99.0/24 subnet and the *.playground.raspwn.org domain.
Network services running in Raspwn include -
- Bind9 (192.168.99.1, 192.168.99.10) - DNS Server
- Postfix (192.168.99.18) - Mail Transfer Agent
- Dovecot (192.168.99.18) - Mail Client Server
- Samba (192.168.99.10) - Windows File Sharing Server
- Apache2 (192.168.99.13) - Web Server
- Nginx (192.168.99.7) - Web Server
- MySQL Server (127.0.0.1) - Database Server
- OpenSSH (92.168.99.1) - SSH server
5- PentestPi
PentestPi is a project that transforms a Raspberry Pi into a pentesting dropbox. It is designed to be deployed in a target network to collect credentials using the Responder tool and transmit them securely to an external listener.
It also establishes a reverse SSH tunnel, enabling remote access to the Raspberry Pi from the internet for further penetration testing tasks.
The setup relies on Kali Linux ARM to streamline configuration, and the scripts reduce the need for manual adjustments across Raspberry Pi devices. It offers a practical, low-cost tool for penetration testers to conduct network assessments remotely and efficiently.
For more details, check the PentestPi repository on GitHub.
6- EtherOS
For Raspberry Pi Zero
EtherOS is an open-source operating system designed to transform the Raspberry Pi Zero 2 W into a powerful, compact tool for penetration testing. Tailored specifically for ethical hacking, it streamlines security assessments by providing essential tools and utilities in an optimized environment.
EtherOS leverages the portability of the Raspberry Pi to offer a lightweight yet effective platform for cybersecurity professionals and enthusiasts, enabling both mobile and remote testing scenarios.
Features
- Compact and Powerful: Unleash the full potential of your Raspberry Pi Zero 2 W for penetration testing.
- Ethical Hacking Simplified: Streamlined tools and utilities for efficient security assessments.
- Raspberry Pi Zero 2 W Compatibility: Tailor-made for the latest Raspberry Pi model for seamless integration.
- Open Source Security: Embrace collaboration and knowledge-sharing within the cybersecurity community.
7- NightPi

This amazing project is based on a Raspberry Pi 3B+ with Kali Linux installed, the "NightPi" is a briefcase designed to learn and perform penetration testing, investigation (OSINT) and radio exploration.
8- Portable Hacking Station RPI
The Portable Hacking Station RPI is a project designed to convert a Raspberry Pi Zero W or Raspberry Pi 3 into a compact device for performing WiFi network audits.
It connects through Bluetooth or mobile data, allowing users to interact with the device remotely using a smartphone via SSH or Bluetooth serial communication.
9- SwissArmyPi Converts your Raspberry Pi into a Strong Hacking Tool
SwissArmyPi is an open-source project (MIT licensed) by Vizay Soni that turns a Raspberry Pi or Pi Zero into a versatile hacking and pentesting tool.
It supports WiFi cracking, phishing with fake access points, and tools like Reaver, Wifite, and Wifiphisher. This project provides a compact, customizable platform for ethical security testing.
Users are responsible for ensuring that they comply with applicable laws and obtain proper authorization before engaging in penetration testing activities. Always use these tools in a responsible and ethical manner. Misuse of these resources can lead to severe legal consequences.
Build More with Raspberry Pi