17 Free MQTT and IoT Protocols Pentesting tools and Frameworks for IoT Security Experts and Pentesters
Table of Content
What is MQTT (Message Queuing Telemetry Transport)?
MQTT (Message Queuing Telemetry Transport) is an OASIS standard messaging protocol specifically designed for the Internet of Things (IoT).
Its lightweight architecture is perfect for connecting remote devices that have limited resources and minimal network bandwidth. This makes MQTT an ideal choice across various industries, including automotive, telecommunications, and manufacturing.
MQTT Key Features
One of the protocol's key features is its ability to facilitate bi-directional communications between devices and the cloud, allowing messages to be easily broadcasted to multiple devices simultaneously.
Additionally, MQTT can scale efficiently, supporting connections with millions of IoT devices without sacrificing performance.
The Primary Component for IoT Messaging
Reliability is crucial for many IoT applications, and MQTT addresses this with three defined quality of service (QoS) levels, ensuring messages are delivered according to the application's needs.
Moreover, MQTT is well-equipped to handle unreliable network connections, making it suitable for devices that operate over cellular networks, as it maintains persistent sessions to reduce reconnection time.
Security is also a priority for MQTT, which supports message encryption through TLS and modern authentication protocols like OAuth. This combination of lightweight design, reliability, scalability, and security makes MQTT a powerful solution for IoT messaging needs.

Why you need to pentest MQTT ?
Penetration testing (pentesting) MQTT is essential for several reasons. Firstly, MQTT is widely used in IoT applications, making it a target for malicious attacks that can compromise device security.
Secondly, the protocol's lightweight nature can lead to vulnerabilities if not properly secured, such as weak authentication and unencrypted messages.
Thirdly, as MQTT supports bi-directional communication, it can be exploited to inject malicious messages or commands.
Finally, regular pentesting helps ensure compliance with security standards and enhances overall network integrity.

MQTT Pentesting Tools and Frameworks
1- MQTT-PWN
MQTT is a lightweight machine-to-machine protocol widely used for IoT devices, enabling efficient publish/subscribe messaging. MQTT-PWN is a comprehensive tool designed for penetration testing and security assessments of IoT brokers.
It integrates enumeration, exploitation modules, and supportive functions, all within an easy-to-use command-line interface, allowing for extensibility and user-friendly operations.
Features
- Credential Brute-Forcer - configurable brute force password cracking to bypass authentication controls
- Topic Enumerator - establishing comprehensive topic list via continuous sampling over time
- Useful Information Grabber - obtaining and labeling data from an extensible predefined list containing known topics of interest
- GPS tracker - plotting routes from devices using OwnTracks app and collecting published coordinates
- Sonoff Exploiter – design to extract passwords and other sensitive information
- Extensibility - the framework was designed to add new custom plugins with ease
- Shodan - search through Shodan.io API for available vulnerable MQTT brokers
2- Moxie - MQTT Pentest Tool
Moxie is a bash script designed for penetration testing of MQTT IoT devices. It allows users to test the MQTT service on a specified target, scan for open ports, and conduct brute-force attacks to assess authentication security.
This tool is useful for identifying vulnerabilities in MQTT implementations.
Features
- MQTT Service Check: Checks if MQTT service is accessible on a specified IP address and port.
- Advanced Scan: Performs an advanced scan using Nmap to gather detailed information about the MQTT service.
- Brute-force Attack: Attempts to brute-force the authentication of the MQTT service using provided username and password wordlists.
3- RabbitMQ
RabbitMQ is a message-queueing software also known as a message broker or queue manager. Simply said; it is software where queues are defined, to which applications connect in order to transfer a message or messages.
4- MQTT Credentials Brute Forcer
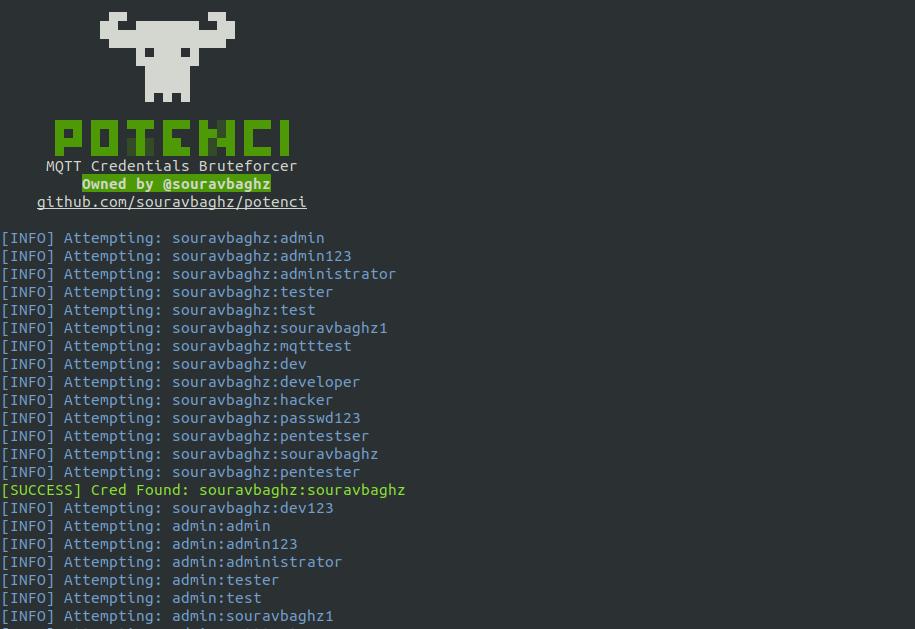
Potenci is a penetration testing tool designed for assessing the security of MQTT brokers and IoT devices. It offers a user-friendly interface for performing various security assessments, including enumeration, exploitation, and testing for vulnerabilities in MQTT implementations.
The tool aims to streamline the penetration testing process, making it easier for security professionals to identify weaknesses in IoT systems.
5- mqtt-packet-fuzzy
The mqtt-packet-fuzzy tool is designed for testing the robustness of MQTT implementations. It uses fuzzing techniques to send malformed MQTT packets to brokers, helping identify vulnerabilities and weaknesses in MQTT services.
6- MQTTack
MQTTack is a yet another penetration testing tool for MQTT protocols, designed to help security professionals assess the vulnerabilities of MQTT brokers. It offers various features such as packet crafting, brute-force attacks, and testing for weak authentication.
7- IOXY - MQTT intercepting proxy
IOXY (IoT + Proxy) is an MQTT intercepting proxy written in Golang. It supports MQTT, MQTTS and MQTT over WebSockets and has both a CLI and a GUI.
8- MQTTSA
mqttsa is a free and open-source powerful tool designed for assessing the security of MQTT brokers and devices.
It allows users to perform various security tests, including vulnerability scanning and protocol analysis, helping to identify potential weaknesses in IoT systems.
9- PENIOT
PENIOT is a versatile penetration testing tool designed specifically for Internet of Things (IoT) devices. It enables users to conduct both active and passive security attacks, targeting device internet connectivity.
Pentesters and IoT security experts can automate various security tests, including resource manipulation and traffic analysis. Additionally, PENIOT is extensible, allowing for the integration of new attacks and IoT protocols, making it a robust framework for IoT security assessments.
10- MQTT Pentest
This is another IoT/ MQTT penetration testing tool focused on assessing the security of MQTT brokers.
It offers various features for scanning and exploiting vulnerabilities within MQTT implementations, allowing users to perform tasks like credential enumeration, message interception, and more.
11- MQTT Exploit and Pentesting
MQTT exploit and Pentesting guide for penetration tester
12- MQTT_DoS_attack
The MQTT_DoS_attack tool is designed to test the resilience of MQTT brokers against Denial of Service (DoS) attacks. It allows security professionals to simulate various attack scenarios, helping identify vulnerabilities in the broker's handling of high loads or malicious messages.
This tool is beneficial for ensuring robust security measures are in place, thereby improving the reliability of IoT systems that rely on MQTT.
13- EXPLIoT (IoT Pentesting)
EXPLIoT is a Python-based framework designed for security testing and exploiting IoT products and infrastructure. It offers a variety of plugins or test cases for conducting assessments, and it can be easily extended with new ones.
The name EXPLIoT cleverly combines "exploit" and highlights the framework's focus on IoT exploitation. This tool is essential for security professionals looking to evaluate the resilience of IoT devices and systems against various attacks.
14- RouterSploit - Exploitation Framework for Embedded Devices
The RouterSploit Framework is an open-source exploitation toolkit specifically designed for embedded devices. It features a range of modules that facilitate penetration testing, including:
- Exploits for targeting known vulnerabilities,
- Creds for testing credential strength,
- Scanners to identify vulnerabilities in targets,
- Payloads for generating attack vectors across different architectures, and
- Generic modules for conducting standard attacks.
15- IoTSecFuzz(ISF
IoTSecFuzz (ISF) is a versatile tool designed for comprehensive security testing of IoT devices. It features a user-friendly console for standalone use and can also be integrated as a library.
The framework operates at three levels: hardware (debugging interfaces), firmware (reverse engineering), and communication (NRF24, Bluetooth, Wi-Fi).
16- HomePwn - Swiss Army Knife for Pentesting of IoT Devices
HomePwn is a pentesting framework designed for auditing and penetration testing of devices commonly used in office and home environments. It features a modular architecture that allows users to expand its capabilities with various discovery modules for technologies like Wi-Fi, NFC, and BLE.
HomePwn helps identify vulnerabilities in these devices by conducting scans and assessing their security levels using specific techniques tailored to each technology.
17- KillerBee
KillerBee is a framework designed for testing and auditing ZigBee and IEEE 802.15.4 networks. The latest 3.0.0-beta update focuses on migrating to Python 3, cleaning up the code, and enhancing functionality. As part of this update, certain features, like usb0.x support, are being deprecated.